Penetration Testing Insights
Professional cybersecurity blog covering penetration testing, ethical hacking, vulnerability assessments, and security research. Learn from expert tutorials, tools, and real-world case studies.
Latest Insights
Stay updated with the latest penetration testing techniques, security vulnerabilities, and cybersecurity trends.
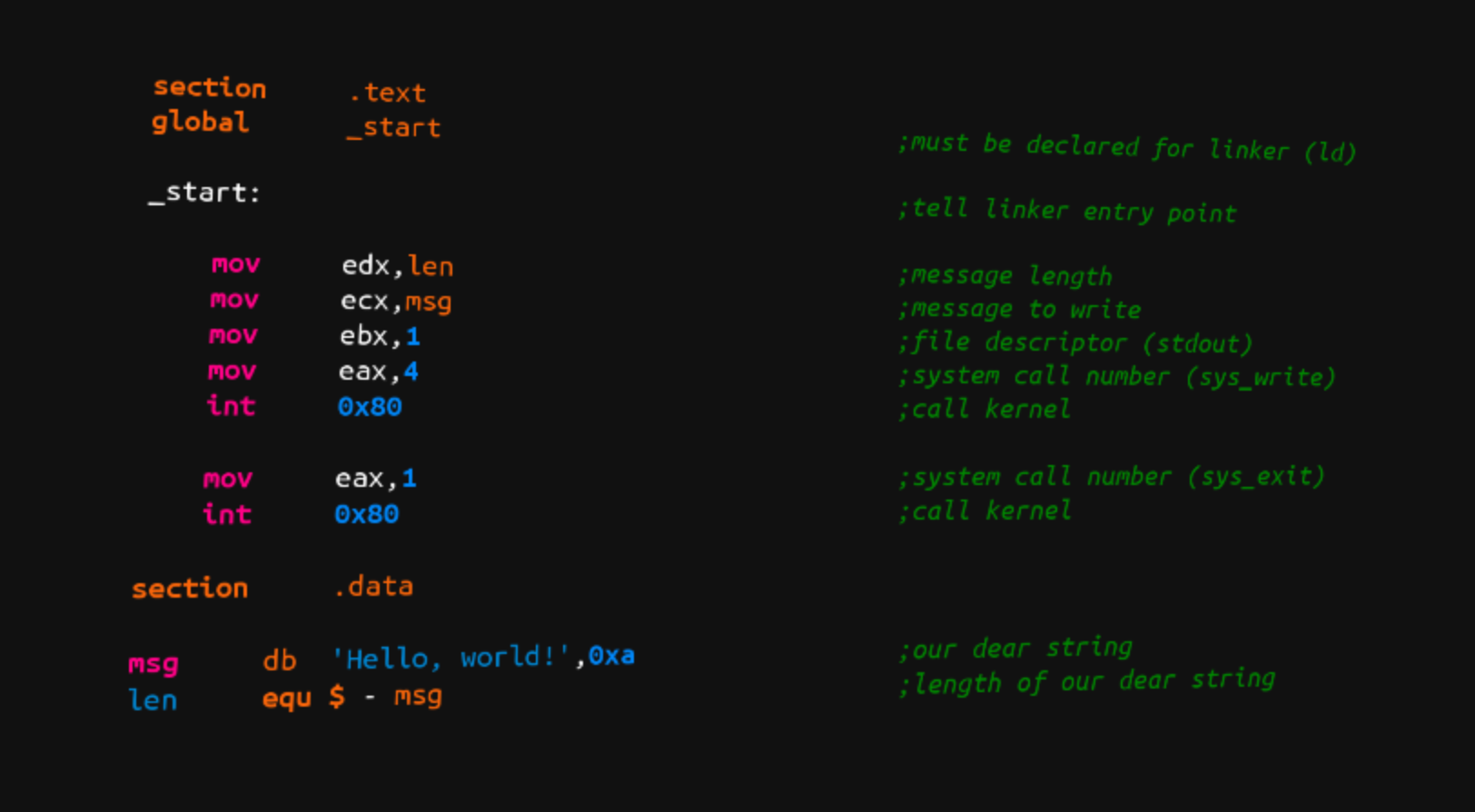
assemblyprogramming
Assembly From Zero
Assembly from zero to hero.
S
By Super Administratornetexecadwindows
Netexec Cheatsheet
A powerful tool used in network penetration testing, especially for Windows environments.
S
By Super Administrator
nmapnetwork-securitycheatsheet
Nmap cheatsheet
This guide covers all the mostly used NMAP commands
S
By Super Administrator